Let Us Make Data Flow
by CPChain at July 30, 2018



Hello everyone. My name is Matthew. I am the tech lead at CPChain.
Today, I am very honored to share with you our latest work, PDash, whose mission is to build a healthy ecosystem that promotes data sharing. In simple words, we want to make data flow between us, between people who have the data to offer and those who need it.
We are now living in a world where IoT data is ceaselessly created every second. It could come from your wearable devices like apple watch, or some health monitoring gadgets; it could also be from your on-board car equipments such as car navigation systems, and dash cameras. But all in all, a natural question is, how can we fully utilize the data, and how can we maximize the economic value inside it?
In an ideal world, we should have full control of our own data. It is an asset of us, no different from other properties like the mobile phones and cars we own. Not only are we the data producer, but also we are entitled the privilege to manage it. Don’t worry, this doesn’t bring you any burden; it only gives you freedom. Infrastructure services such as PDash does the heavy lifting, and what you do is just sit down, relax and enjoy all the flexibilities that come along.
You have the rights and capability to freely access it, modify it, and most importantly, share the data with others. You, as the owner, decide who has the permission to see the data. What’s more, you can even trade the data for profit.
There is no barrier to conduct such a trading. For one thing, information describing the data is completely open and transparent. Different from the financial industry, brokers services are completed eliminated in IoT data sharing. Specialized marketplaces are setup here. People can publish data description on the market, and later, potential users can readily query for it. For another, the actual data transmission between users is strengthened and simplified. The transmission is supervised and coordinated by dedicated relay services, so that abrupt network failure or harsh network environment won’t abort the sharing.
Last but not least, throughout the trading process, our economic rights are fully protected. A set of regulation rules are enacted, which encourage people to join the ecosystem, incentivize and reward the participants for offering high-quality data. On the other hand, fake data is recognized and rooted out in the system. In case fraudulent actions do happen, the system will ruthlessly punish those who cheat, confiscating their 通证s, and meanwhile compensate those suffering financial loss.
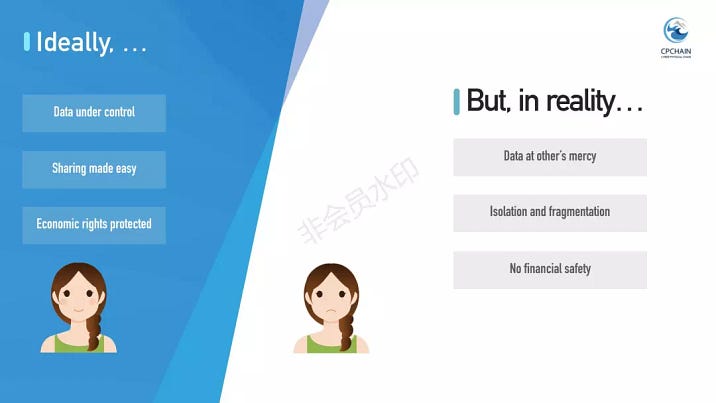
The first issue is personal data privacy.
IoT data is everywhere, but it is not in the hand of the end users. Instead, vendors, large corporations and governmental organizations own the data, leaving users at their mercy. This poses severe privacy and security risks.
What if they change the ToS and limit our access to the documents? What if they peep into our private images? Such worries are not imaginary, and we all remember the pain of the Facebook data leak.
The second issue is data isolation.
Information silo is not uncommon for IoT data. Manufacturers build devices that are of heterogeneous architectures and speak inconsistent protocols, Actually, we are facing a predicament where data are held and segregated by different systems. Its value is completely undermined under such isolation. For example, data collected from your wearable devices has little help to medical treatment in the hospital. One thing is that, it’s hard for the hospital to access your data; and further, they don’t even understand the format and semantics of your data.
While users’ economic rights are protected in the ideal world, this is quite the opposite in reality. Data quality is not warranted and it’s hard to get money back when frauds happen. For example, if a consumer buys fake data, once money is transferred to the other side through bitcoin, it is impossible to get the coins back. You call the policeman for help, but probably they will say it’s not regulated by the law. However, things shouldn’t go this way.
Fundamentally, we lack a formal sharing model, an economic model that eradicates those fraud actions, and promotes the sharing of high-quality data. The participants that are well-behaved must be rewarded, hence attracting more obedient people to join the community. Those that offering fake data must be punished and expelled from the ecosystem.
The concept of IoT has been around for years. It has great vitality and is affecting us in every aspect of life. However, it also seems to have reached some bottlenecks: data are under centralized control, fragmented, and lacks a sharing model.

Aside from the sad reality, however, there are still some good news happening to us.
One thing is software-defined hardware. We have seen software-defined network, software-defined radio, and software-defined robot. By programming the hardware, we are given the rights, and can easily retrieve data from the hardware with uniformed API. That is, data is no longer locked by the vendors; users can also access it. By the way, some car companies are recently in contact with us. They want to cooperate with us by providing the API o f its OBD devices.
Another improvement is commodity data storage. Users only need pay an affordable and small amount of money to hold their own data on cloud drives such as Amazon glacier, dropbox, and IPFS.
Last but not least, the development of blockchain technology has made it possible to carry out direct money transfer. While there are some security and efficiency obstacles, the future is promising.
Equipped with the above technologies, it seems we have reached an inflection point where, if we take one step further, we are able to enter the ideal data sharing world.

Now, here is the question, how do we take that step? How do we bridge the gap between data providers and consumers, and make data flow?
Well that step is PDash.
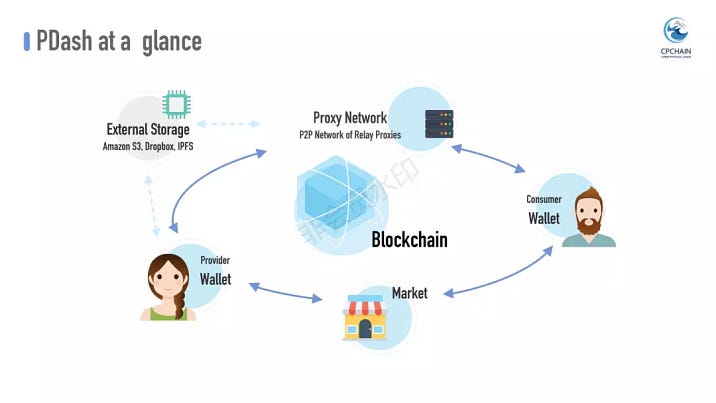
Here is a bird’s eye view of the PDash platform.
To the end of connecting data providers and consumers, PDash, proposes, several, innovations, the wallet, market, proxy network and chain.
In addition to managing token assets as seen in conventional blockchain wallets, PDash wallet puts a focus on the safety of data and facilitates the whole sharing lifecycle.
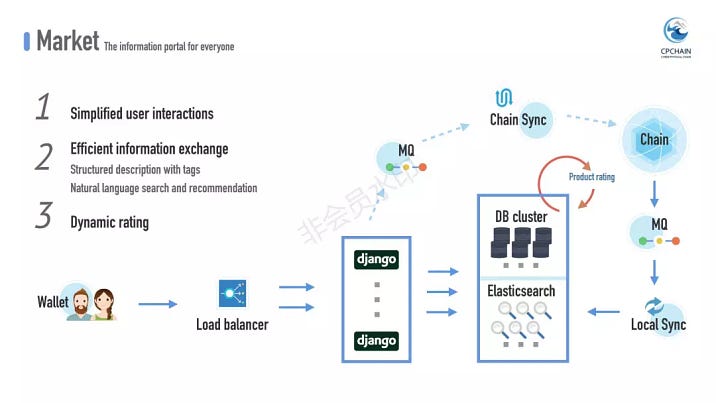
The PDash market acts as an information portal, eliminating the barrier between data providers and consumers. Users can publish and query for data on it.
The de-centralized proxy network is also indispensable. It safeguards the actual data relay from external storages to the buyers.
Above all, the CPChain blockchain, with our specially tailored smart contracts, unites them together and makes the magic happen.
Now we take a deep look into each component.
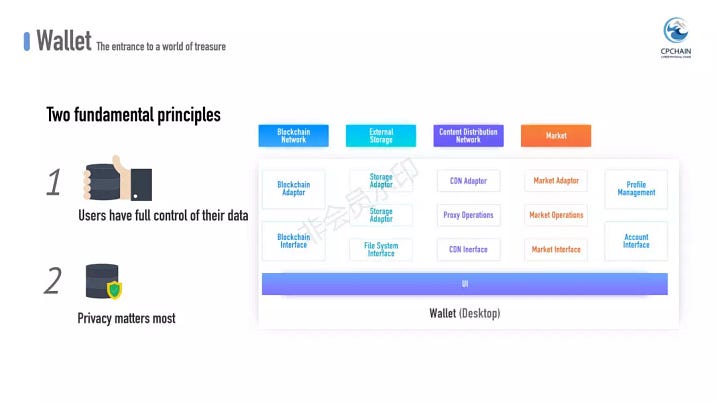
Compared with current online markets, one advantage of PDash is that, it greatly simplifies user interactions. Username and password are no longer required; digital signature with elliptic curve handles all of the labour work like registration and authentication. Armed with cryptographic techniques, your private and public key act as the passport in the market.
Another advantage lies in the preciseness and efficiency in information exchange between data providers and consumers. The data providers can freely describe data and publish it without losing semantics, and consumers can query it without hassle.
On PDash market, data description is abstracted from different categories of data, ranging from IoT ones to user-produced electronic documents. The market supports structured description with tagged keywords. The provider can add tags such as the industry field of the data, term of use, and the copyright.
To allow for accurate and targeted information retrieval, the consumer is able to search for interested data with natural language. What’s more, the market can recommend users relevant data. Under the hood, the market integrates the elasticsearch engine and makes use of tailored recommendation algorithms.
It’s worth to point out that, while we strive to maximize data’s value by sharing it with the vast users, illegal and offensive data are strongly discouraged. For that purpose, we adopt a dynamic rating mechanism that degrades those items in time.
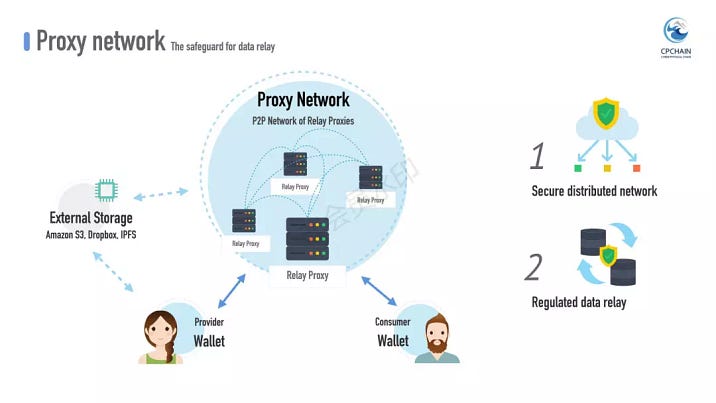
Proxy network plays a critical role in transferring data to consumers. It is the safeguard for data relay. After a proxy is agreed upon by the provider and consumer, it then moves forward the whole sharing process. It fetches data from the external storage on behalf of the provider, and then informs the consumer to retrieve data from it.
Take the proxies as a whole, they form a DHT-based self-organized distributed network. When a proxy malfunctions, another will immediately take its place.
To enhance the security of the network, we again embrace elliptic curve based cryptographic strategies. Each proxy possesses a unique identifier in the network. When it broadcasts a message, the receive sides will examine the message’s validity by verifying its signature and other auxiliary information.
One type of messages is the so called addressing message. Proxies announce their addresses in the DHT network; hence, the data providers and consumers needn’t query a central registrar for a proxy’s location. It is worth to note that, providers and consumers are free to choose their liked proxy for the relay, but we have also built a recommendation service that suggests proxies appropriate to them.
From the point of each proxy, once selected, it officiates in the relay process, auditing transmissions and guarding the rights of both sides. As a third-party arbitrator, the proxy can judge if the provider or consumer misbehaves. For example, the proxy can examine the validity of the data address offered by the provider.
In case a fraudulent transaction happens, the proxy is entitled to settle the dispute with predefined smart contracts.
The added benefits of proxies are not limited to the above, for example, we can:
Speed up data transmission with geo-aware proxy selection.
Fine tune data access control for the consumers.
And also conduct anonymous data usage statistics.
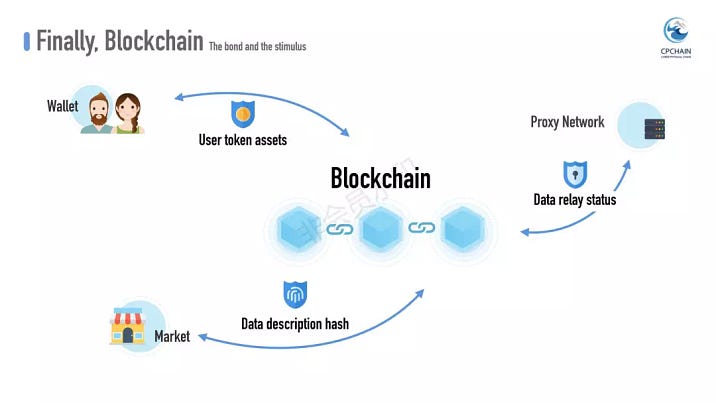
So far we have skirted around the most essential part of PDash, that is the chain. For one thing, it closely bonds together the wallet, market, and proxy network. For another, it stirs around the whole system, incentivizing data sharing with economic reward, but also punishes those misbehave.
PDash is the first chain project that seamlessly inter-connects the ingredients vital to data sharing. The chain records critical information and carries out smart contract operations for the participants. For wallet, it manages user’s 通证 assets; for market, it attests the data description with its hash value; for proxy network, it monitors data status in the complete relay lifecycle. All in all, the chain serves as the single immutable and irrefutable authority for both online and post-mortem transaction tracking.
One design philosophy behind PDash smart contract is to create an open and lively ecosystem. It encourages users to trade data on the platform, rewarding them according to their service quality and mercilessly punishing the cheats.
Consumers pay tokens to trade data. Those tokens are then temporarily held by the smart contract. After the trading has successfully completed, the tokens will flow to the provider and the relevant proxy, where the exact proportion depends on the service type. However, if the provider sells fake data, the smart contract will abort the transaction and further, confiscate the tokens pre-deposited by the provider.
This healthy model attracts people to join in, bonds them together, and makes data flow between them.
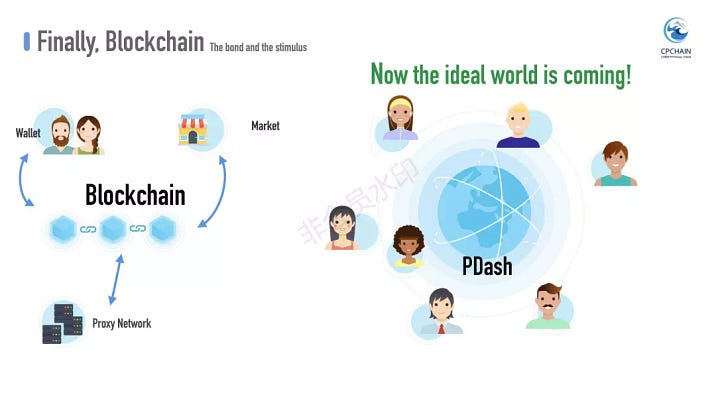
So far, we hope you have got a detailed understanding of PDash, the highlights and its immeasurable potential.
To recap, PDash presents:
- A fully-fledged wallet that brings data to the vast users
- An open market that connects data providers with consumers
- A distributed proxy network that safeguards data relay
- A chain that unites and stimulate all data sharing participants
For us, the release of PDash is more of a start than an end. In fact, we are all exhilarated to venture further into this data sharing realm. Especially, as we are actively developing our own blockchain, the main chain and side chain, we are going to integrate deeper with these specialized chains.

One of our future directions is decentralized market.
In the current version of PDash, transactions already operate in a decentralized manner. Even if the market is offline, users can still trade data as long as the consumer knows the market hash of the data.
Of course, when the market is down, providers cannot publish new data descriptions, and consumers cannot query for it. To improve user experience, we decide to break this status quo, and plan to develop the world’s first blockchain powered decentralized market. Instead of a single market run by us, certified participants can join this network and launch their own market. These markets share the same view, where the actual data storage is distributed and synchronized on the blockchain.
So open your eyes and stay tuned.





