CPChain Bug Bounty Program on the Way
by CPChain at May 16, 2019

The motivation behind the CPChain Bug Bounty Program is to use the open source nature of our undertaking to improve our blockchain's security. This will be an open door for security analysts from around the globe to discover and report potential security bugs identified with our fundamental framework. At the point when a bug is found, please don't hesitate to report the issue towards CPChain Github by following the configuration we have itemized in this post. We will attempt our best to explore every single qualified bug, and fix any substantial issues. All prizes for our Bug Bounty Program will be paid in the identical measure of CPC.
Following is the submission link:
https://github.com/CPChain/chain/issues
(A Github account is a prerequisite)
Note: Higher rewards will be paid out for bugs of certain interest and severity. Before reporting any issues, please check the following disclosures and guidelines on responsibilities, program rules, and report structure.
Program Rules
The dimension of each bug's seriousness will experience assessment by the CPChain R&D group dependent on impact, influence and numerous different perspectives. As we will organize report evaluation by risks and different elements, it may take some time for our response. The normal time to our first reaction (from report submission date) will be 5 business days; time to triage (from report submission date) will be 10 business days. CPChain will do our best to keep the network and dynamic security analysts required by consistently refreshing the criticism on our site and internet-based life channels. Prizes will be dispersed within 7 days following an official declaration. CPChain reserves the right of final interpretation of the event.
In order to earn the applicable reward, the submitters should abide by the following event rules:
- Only issues identified with the stability and security of design and implementation is within the scope of this event, bugs on the CPChain website and other related infrastructure on the CPChain blockchain is out of the scope. Discover more subtleties at the Scope of Bug Bounty Program area of this post.
- Submitted reports ought to contain detailed reproduction procedures, without which, the reports will be rejected from the reward list. The more detail the reports contains about the proof and depiction of the bug, the higher your reward will be.
- For those who report the same vulnerability, the reward goes to who reports the vulnerability to CPChain first.
- Serial bugs caused by one vulnerability will be considered as one vulnerability, e.g., a series of computing errors caused by data overflow.
Bugs fitting in any of the following descriptions will not be eligible for the rewards:
- Those previously published or known are not eligible for rewards.
- Bugs unveiled before CPChain fixes or publishes them are not eligible for rewards.
- Participants who use submitted bugs to damage the CPChain ecosystem, infringe on users’ interest and perform pilferage on users’ assets will be disqualified from receiving any rewards; meanwhile, CPChain reserves the right to take legal action against any such participant.
Scope of Bug Bounty Program
Security vulnerabilities of the following projects are within the scope of the Bug Bounty Program and must be addressed in the report to be eligible for rewards:
- CPChain --- Chain
- CPChain --- Wallet
Investigating and reporting vulnerabilities
Please, never attempt to access anyone else's data and do not engage in any activity that would be disruptive or damaging to CPChain’s production network and testing network, you can investigate with your own private chain.
Please include the following in your report:
- Asset - What software asset the vulnerability is related to (e.g. CPChain core software/products)
- Severity - Your opinion on the severity of the issue (e.g. critical, high, medium, low)
- Summary – Add a detailed summary of the vulnerability
- Description - Any additional details about this vulnerability
- Steps - Steps to reproduce the vulnerability, clearly explain every detailed step to the CPChain team
- Supporting Material/References - Source code to replicate, list any additional material (e.g. screenshots, logs, etc.)
- Impact - What security impact could an attacker achieve?
- Your name,email and country.
Duration for Season 1
Starting from 5/1/2019, it will end on 11/20/2019.
Rewards
Bounties are paid out after a risk assessment (OWASP risk rating methodology) has been made by our R&D team. There are four rates of severity, Critical, High, Medium, Low. All rewards will be paid in the equivalent amount of CPC. Roughly speaking, we calculate the severity of an issue with the following formula:
Bounties are paid out after a risk assessment (OWASP risk rating methodology) has been made by our R&D group. There are four rates of seriousness, Critical, High, Medium, Low. All rewards will be paid in the comparable measure of CPC. Generally, we ascertain the seriousness of an issue with the accompanying recipe
Severity = Impact * Likelihood
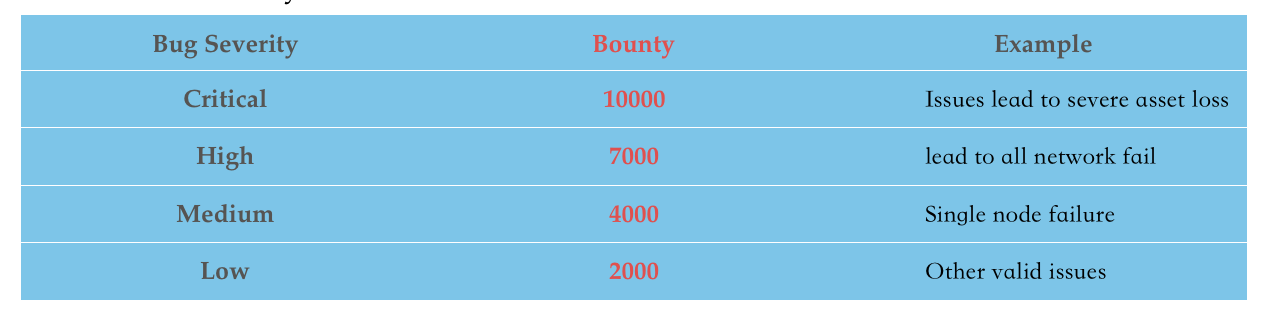
The base bounty reward structure after risk assessment is as follows:
Thanks for sticking with us. Thanks for the Long term support. Patience will pay off.
Sincerely,
CPChain Team

Community Events
Tutorials on How to Test the CPChain Alpha Mainnet
CPC faucet is an application that you can collect CPC test coins for free. The test coins can be used in newly-published CPChain Alpha Mainnet. Refer to https://cpchain.io/faucet/ to try it now.

CPChain
Jan. 11, 2019



