CPChain — PDash Platform: IoT Data Exchange Solution
by CPChain at June 27, 2018


What is the PDash Platform?
CPChain has been hard at work placing the final touches on the beta release of our PDash platform. It is now time to share our progress with our community.
PDash, short for Parallel Distributed Architecture for Data Storage and Sharing, aims to bridge the information gap between data providers and consumers while maximizing the economic value of data. This will be accomplished by developing solutions for data security, privacy, fragmentation, and by conveying the benefits of the innovative data-sharing platform to all participants.
Before we take a deep dive into PDash, let’s quickly review the current issues found in IoT (Internet of Things) industry.
Current IoT Industry Issues
While we have observed immense development and adoption in the IoT industry, data sharing remains difficult issue in regards to administration and development. The recently passed General Data Protection Regulation (GDPR) aims to provide personal data control to citizens and to simplify the regulatory environment for international businesses. The GDPR has ignited heated discussions and has led to various different views on data sharing.
“While it has the power to change our everyday lives, IoT remains fragmented and comprised of various incompatible systems, fraudulent data, and risky open network sharing that can lead to a breach,” — Dr. Long Chengnian, CEO of CPChain
Data Security and Privacy
Data is produced by devices everywhere and it’s very lucrative for businesses to analyze. While IoT data is everywhere, it is not in the hands of its producers which are primarily the end users such as you. Instead, large corporations and governmental organizations own the data and use it to profit at the end users expense.
What if these organizations change their Terms of Service and limit our access to the data? What if they search through your private images without your permission? These examples are taking place every day and there is little you can do about it. The most recent example is the Facebook data leak that happened where approximately 87 million users’ personal information was inappropriately shared.
The effects of owning our data will continue to develop over the next few decades. We believe that if we want to have an effect on how this conversation unfolds, there is no better time than now.
Data Fragmentation
Information silos are information management systems that are incapable of freely communicating with other information management systems. These silos are common in the IoT field as the systems have not been created to interact with each other. Manufacturers build devices that are of heterogeneous architectures and communicate with inconsistent protocols, therefore leading to isolated data storage.
For example, in order to improve the curative effect, we should calibrate medical equipment with the massive quantity of data collected from wearable monitoring devices. We should also, in turn, adjust the wearables based on the diagnoses of the medical equipment to make the monitoring more targeted. However, we are facing a predicament where the data is held and segregated by dissimilar systems. The value of data is completely undermined under such isolation.
Data Sharing Model
A fundamental issue confronting IoT data exchange is the lack of a formal sharing model. This raises two important concerns:
- How to incentivize and reward the participants in the sharing process?
- How to recognize and root out fraudulent actions?
Unfortunately, answers to the above questions remain unanswered. Typically, the user pays additional costs to the broker for searching for and buying targeted data. These costs also apply to users who request to sell data. Furthermore, in the current data sharing model, the data quality is not assured and it is difficult for the buyer to obtain a refund when inaccurate or inadequate data is received.
The concept of IoT has been around for years. It has great vitality and affects us all even without us noticing. However, it also seems to have reached some bottlenecks as the data is under centralized control, fragmented, and lacks sharing incentives.
The IoT industry requires an innovative platform for data sharing in order to solve these present-day issues. In order to advance the development of data sharing within the IoT industry, CPChain has developed the PDash platform based on Blockchain technology.

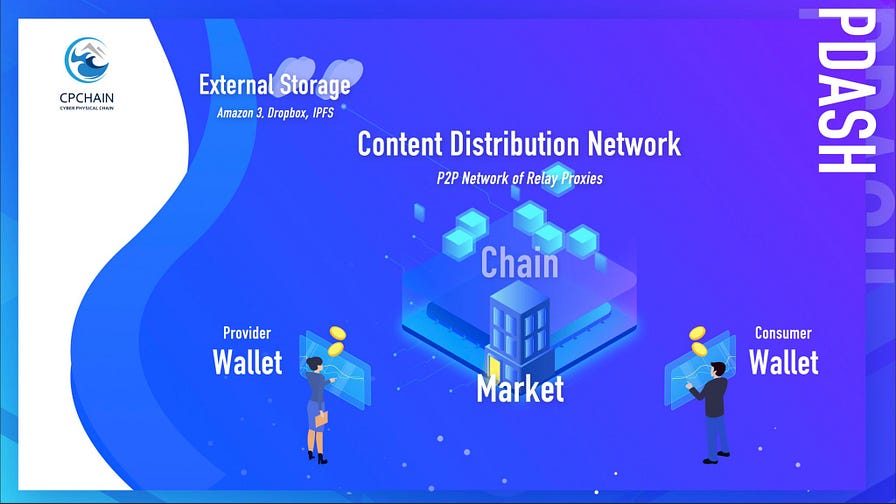
Components of the PDash Platform
In order to connect data providers and consumers, PDash presents several innovations based on Blockchain technology. These innovations include an efficient data wallet, open marketplace, distributed proxy network, and decentralized data storage.
While managing token assets as a conventional blockchain wallet, the PDash wallet is also developed with a focus on the value of data and the data sharing life-cycle.
PDash marketplace functions as an information portal, eliminating the barriers between data providers and consumers.
The decentralized proxy network safeguards the actual data relay from external storages to the buyers.
The CPChain Blockchain platform unites these innovations in order to develop a solution to connect data providers and consumers, to solve isolated data storage, and to cultivate an innovative data sharing platform.
Wallet — entrance to a world of data
The PDash wallet provides the frontend for our data sharing platform. The wallet offers data providers and consumers with solutions to satisfy all industry requirements.
These solutions include encrypting and decrypting user data, offloading data to a distributed storage platform, data description for publishing and retrieval, and most importantly facilitating the entire lifecycle of data sharing.
Data security and privacy is one of the core issues in the current IoT industry and also an utmost concern for CPChain. Due to this concern, the PDash wallet has followed two fundamental principles:
1. Users will have complete control of their individual data.
2. Data will be unconditionally secured with advanced cryptographic algorithms.
We support an array of backend storage platforms such as Interplanetary File System (IPFS) and Amazon S3 to store large data assets. We are also actively developing the CPChain Open Transmission Protocol (COTP), which allows our platform to use an infinite amount of backend solutions as long as they speak the protocol.
The PDash wallet enforces data encryption before offloading to the backend storage platform in order to prevent any data leaks. For increased efficiency, large data is encrypted with symmetric encryption schemes. In the sharing process, the symmetric key is encrypted with the counterparts’ RSA public key; therefore preventing any third-party from viewing the data.
The wallet features several additional developments such as a pleasant user interface and multiple-account management system. We are confident that both providers and consumers will appreciate these features.
Market — data sharing melting pot
The PDash marketplace is developed for everyone with attention to privacy and security. There are no barriers involved in user registration and authentication; a digital signature with elliptic curve handles all of these functions. Data providers can also freely describe and publish data without loss semantics loss, while consumers can query for data without difficulty.
Data description of the PDash market is abstracted from different categories of data, ranging from IoT produced data to electronic documents. The market supports structured description with tagged keywords. The data provider can add a description to self-owned data that is offloaded to the external storage backend. Once the compulsory structured fields for certain data types are filled, the provider can then tag it with its industry, terms of use, copyrights, etc. The description is then published in the marketplace.
In order to allow for accurate and targeted information retrieval, the consumer is able to search for targeted data with natural language. Furthermore, the market can recommend users with relevant data. The market also integrates the elasticsearch engine and makes use of tailored recommendation algorithms. After targeting and retrieving data, the user can purchase the data and an order will be initiated and recorded on the CPChain blockchain.
While we strive to maximize the value of data by sharing it with a vast number of users, illegal and offensive data are strongly discouraged. For that purpose, we adopt a dynamic rating mechanism which degrades that type of data over time.
Proxy Network — safeguard for data relay
The distributed proxy network plays a critical role in relaying data from providers to consumers. The proxies form a DHT-based, self-organized, distributed network. When a proxy malfunctions another will immediately take its place. Each proxy officiates in the relay process, auditing transactions and guarding the rights of both parties.
In order to enhance the security of the distributed network, we embrace elliptic curve based cryptographic strategies. Each proxy receives a unique identifier, compatible with an Ethereum account address, within the network. When the proxy broadcasts a message, the receiving sides will examine the validity of the message by verifying the signature and supplementary auxiliary information.
An example of a message is an addressing message. Proxies announce their addresses to the DHT network so data providers and consumers don’t need to query a central registrar for the location of the proxy. It is worth noting that providers and consumers are free to choose their liked proxies for the relay; however, we have also developed a recommendation service which promotes appropriate proxies.
Once a proxy is agreed upon by the provider and consumer, the proxy moves forward to the data sharing lifecycle process. The proxy fetches data from the external distributed storage on behalf of the provider and then informs the buyer to retrieve the data.
The introduction of the distributed proxy network with admission control conveys a multitude of possibilities. It is also able to ensure consistent accessibility of data and offer the following solutions:
— Data is intact and has the same hash value as the description on the market.
— Data can be readily retrieved by the consumer.
The proxy has the power to settle disputes for fraudulent transactions with pre-defined smart contracts. The benefits of the proxy network also include:
— Faster data transmission with a geo-aware proxy selection.
— Fine tune data access control. For example, the file can only be downloaded within i days, at most j times, from k distinct IP addresses, etc.
— Ability to conduct anonymous data retrieval statistics.
Chain — the bond and the stimulus
The most essential fragment of PDash is the chain; closely bonding together the wallet, market, and proxy network. The chain brings together the entire system, incentivizing data sharing with economic reward while punishing those who misbehave.
PDash is the first chain solution which seamlessly interconnects the various solutions vital to a data sharing and storage platform. The chain records critical information and carries out smart contract operations for participants.
The chain manages the users’ token assets in the wallet, attests the data description with its hash value in the market, and monitors data status in the complete relay lifecycle for the proxy. The chain serves as the single immutable and irrefutable authority for transaction tracking.
One design philosophy behind the PDash smart contracts is to create an open and lively ecosystem. We achieve this by encouraging users to trade data on the platform, rewarding them according to quality of service, and punishing any users who attempt to fraud the system.
Consumers pay tokens in order to trade data, these tokens are then temporarily held by the smart contract. Once the trade has successfully completed, the tokens will transfer to the provider and the relevant proxy.
If the provider sells fake data the smart contract will then abort the transaction and confiscate the sellers’ pre-deposited tokens. Discerning fraudulent data and maintaining security is solved by the dedicated mechanism in our smart contract and proxy network.
“PDash addresses these major hurdles by connecting data providers and users more efficiently and securely via a chain that unites and stimulates all data sharing participants. We’re excited to give our fans and future users an inside look at our innovative platform.” — Dr. Long Chengnian, CEO of CPChain

We hope you have a detailed understanding of PDash, the highlights, and the immeasurable potential it presents for data sharing and the IoT industry. Please read the PDash Technical Paper for further details.
To recap, PDash presents:
- A fully-fledged wallet that brings data to the vast amount of users
- An open market that connects data providers with consumers
- A distributed proxy network that safeguards data relay
- A chain that unites and stimulates all data sharing participants
The PDash launch is more of a beginning than an end. We are exhilarated to venture further into this data sharing realm. In the coming future, PDash will bring you an open storage ecosystem, distributed market system, and deeper integration with industry-specialized sidechains.
Open your eyes and stay tuned.
Matthew Ma
Technology Director
CPChain
To learn more about the code:
GitHub
To learn more about CPChain:
Twitter | Telegram | Reddit | Discord | GitHub | Youtube | WeChat






